Security
Meet our it security solutions
High-expertise IT security company
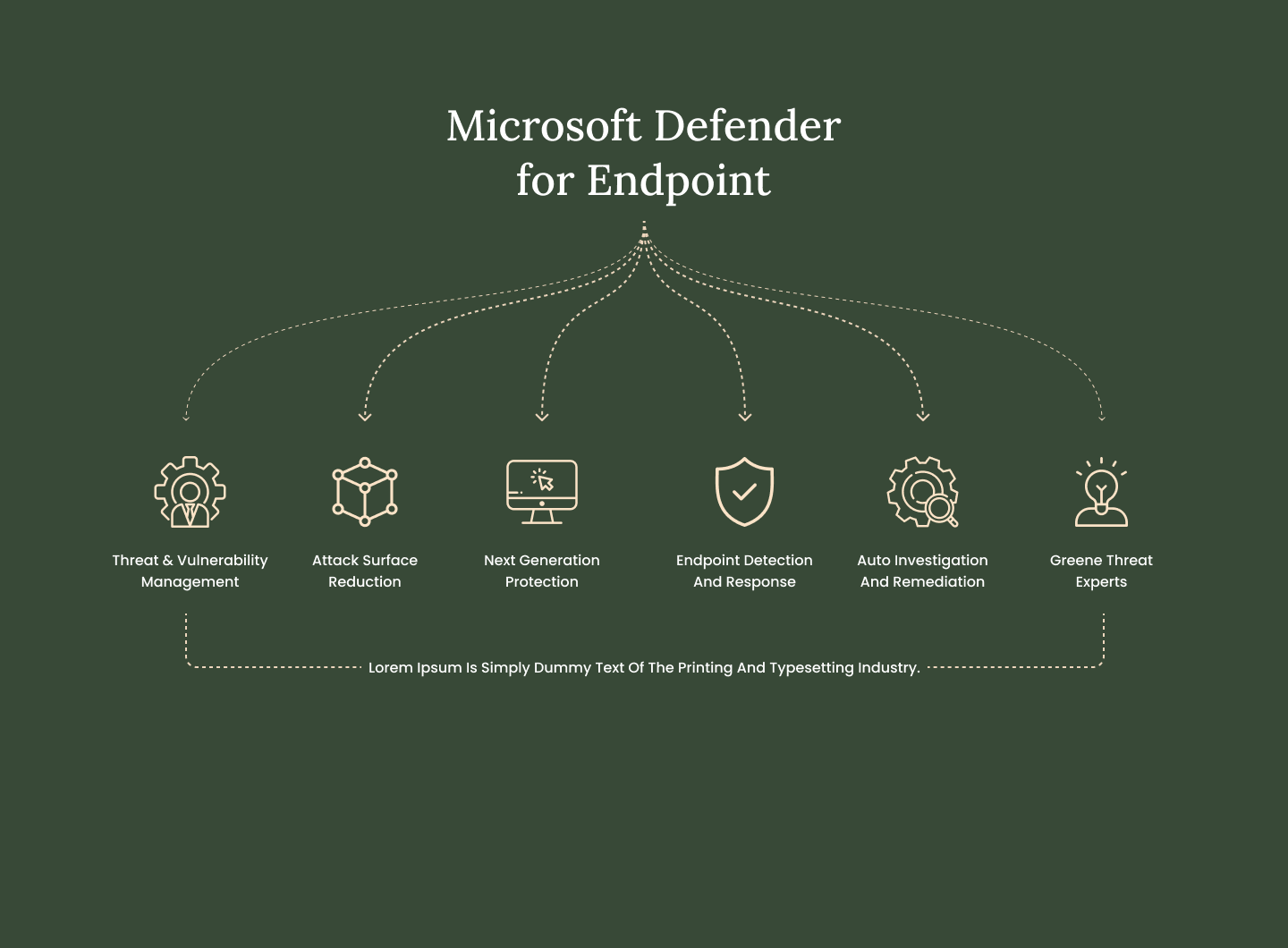
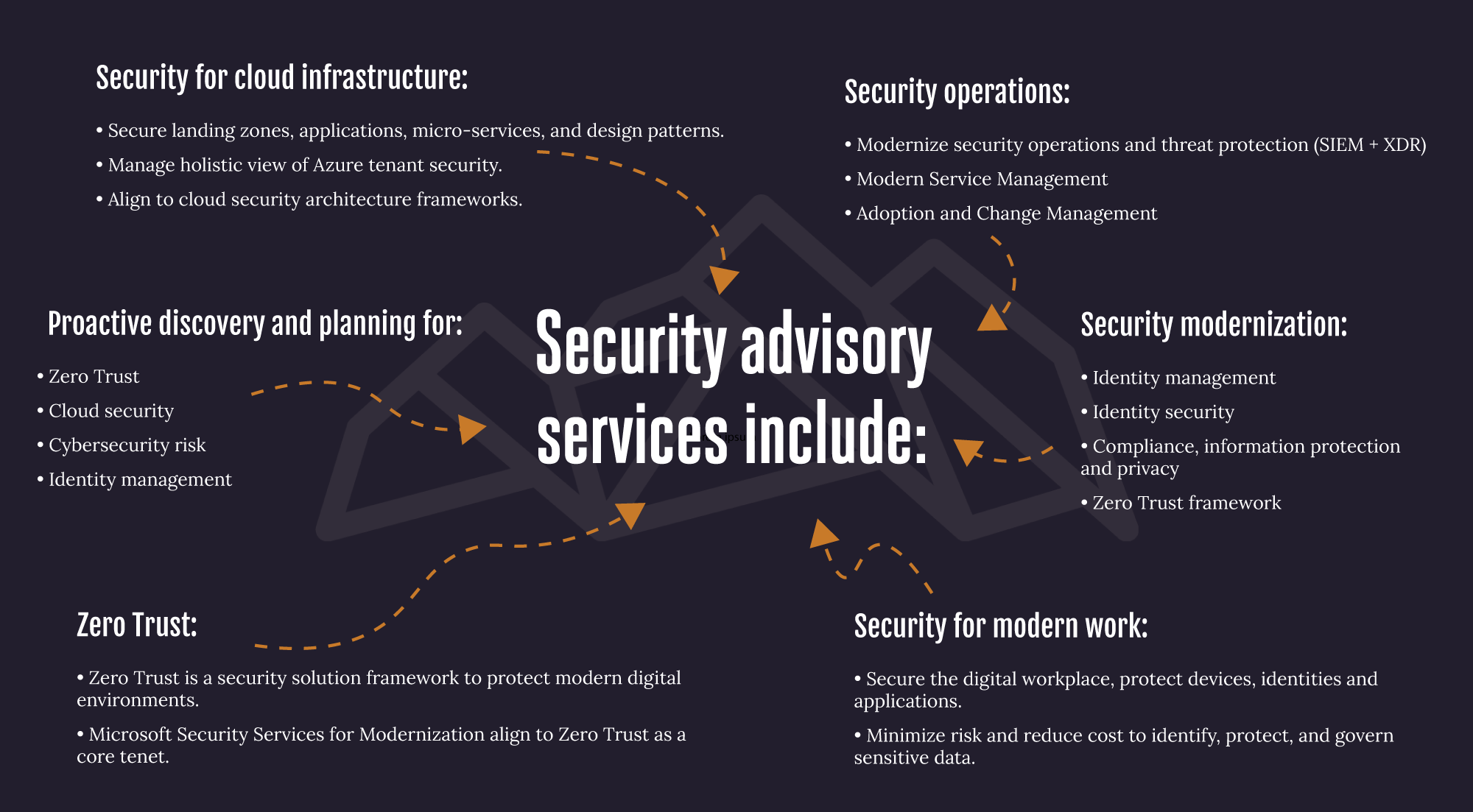
Greene Security Services for Modernization was created for customers that want to leverage Microsoft best practices and know-how as they embrace new modern security capabilities and embark on their security transformation. This service provides in-depth consulting that help customers at any stage of their security journey to modernize their security posture and embrace a zero-trust approach.
- NIST 800.171 800.53
- ISO
- AVD’s
- Government Contracts/ITAR/GCC-High
Rapidly stop threats
Gain the upper hand against sophisticated threats like ransomware and nation-state attacks.
Scale your security
Put time back in the hands of defenders to prioritize risks and elevate your security posture.
Evolve your defenses
Advance beyond endpoint silos and mature your security based on a foundation for XDR and Zero Trust.